Itarian
Product description
We, Hidde Smit and me (Wietse), have discovered multiple vulnerabilities within Itarian.
Vulnerabilities in the following products have been found:
- ITarian SaaS platform
- ITarian on-premise (version 6.35.37347.20040)
- Endpoint Manager Communication Client (version 6.43.41148.21120)
ITarian is a Remote Monitoring and Management (RMM) software suite. It allows administrators to manage endpoints. Because of this powerful position within an organisation, RMM suites are often targeted by malicious actors.
Making initial contact with ITarian proved to be difficult. The vulnerabilities were discovered in December 2021. However, contact and subsequent fixes only started rolling out in May 2022.
Cross-Site Scripting in ITarian SaaS Service Desk module (ITarian SaaS platform)
In order to exploit this Cross-Site Scripting (XSS) vulnerability, the victim needs to enable the Service Desk module, which is not enabled by default.
The vulnerability can be exploited by visiting the victim’s Support Ticket System page as shown in the screenshot below.
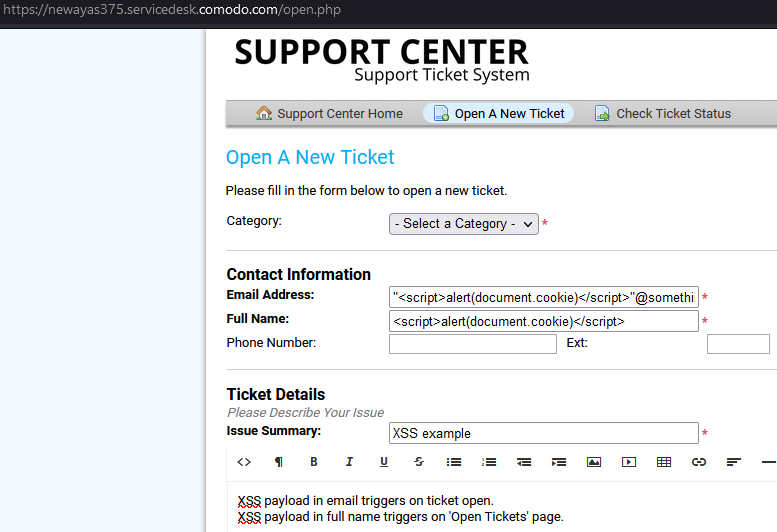
There are two XSS vulnerabilities. One is present in the Email Address field and the other in the Full Name field.
The payload for Email Address is: "<script>alert(document.cookie)</script>"@something.somewhere
The payload for Full Name is: <script>alert(document.cookie)</script>
The Email Address payload triggers once an ITarian MSP user has opened the ticket contents as shown in the screenshot below, the ticket might also trigger if the user hovers over the ticket to preview the content.
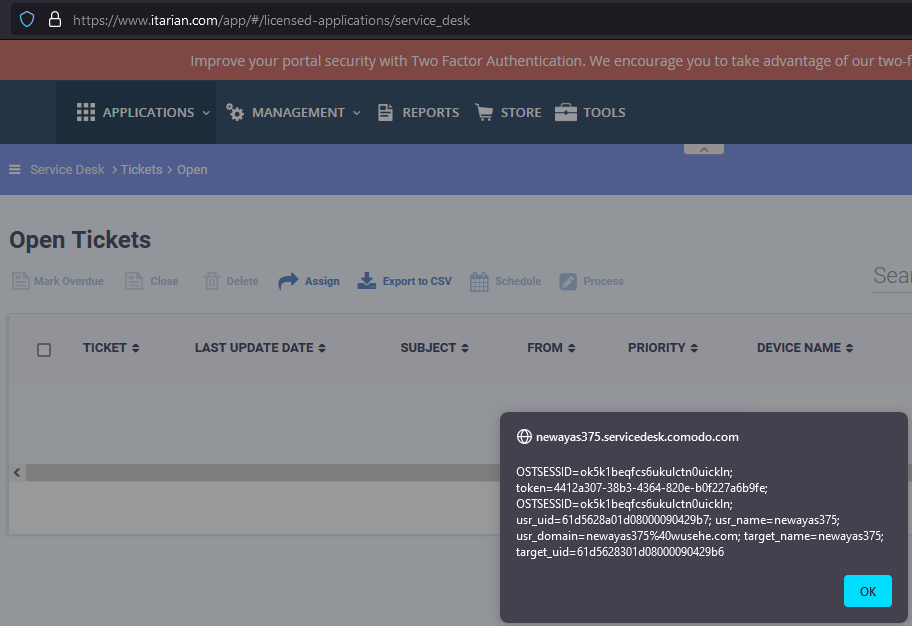
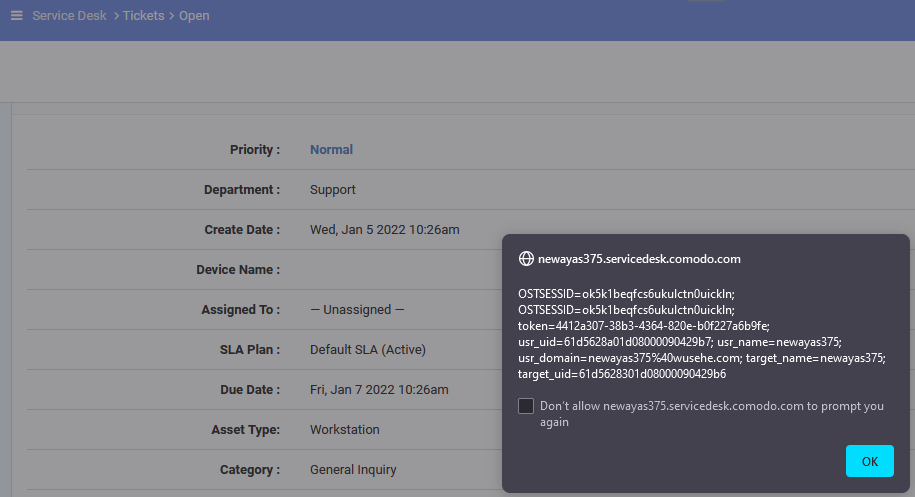
Using this exploit technique, it is possible to steal the ‘OSTSESSID’ cookie and gain access to the ticketing system of the victim by visiting the direct URL, in this case: `https://newayas375.servicedesk.comodo.com/scp/tickets.php
The cookie ‘token’ can also be stolen, which is actually a SSO-token granting full access to the MSP dashboard without any credentials needed. This can be done by stealing the ‘token’ cookie through XSS as demonstrated above and placing it in the MSP URL as shown below:
https://newayas375.cmdm.comodo.com/?sso-token=4412a307-38b3-4364-820e-b0f227a6b9fe
Links
CVE’s
The following CVE’s assigned to the on-prem version:
- 1 Click RCE on all agents May 11
- CVE-2022-25153 - ITarian Endpoint Manager agent local privilege escalation May 11
- CVE-2022-25152 - Creation of procedure and bypass approvals by any user with a valid session token (ITarian SaaS platform / on-premise) May 11
- CVE-2022-25151 - Session cookie not protected by HttpOnly flag (ITarian SaaS platform / on-premise) May 11